How does Sensorfact secure my data?
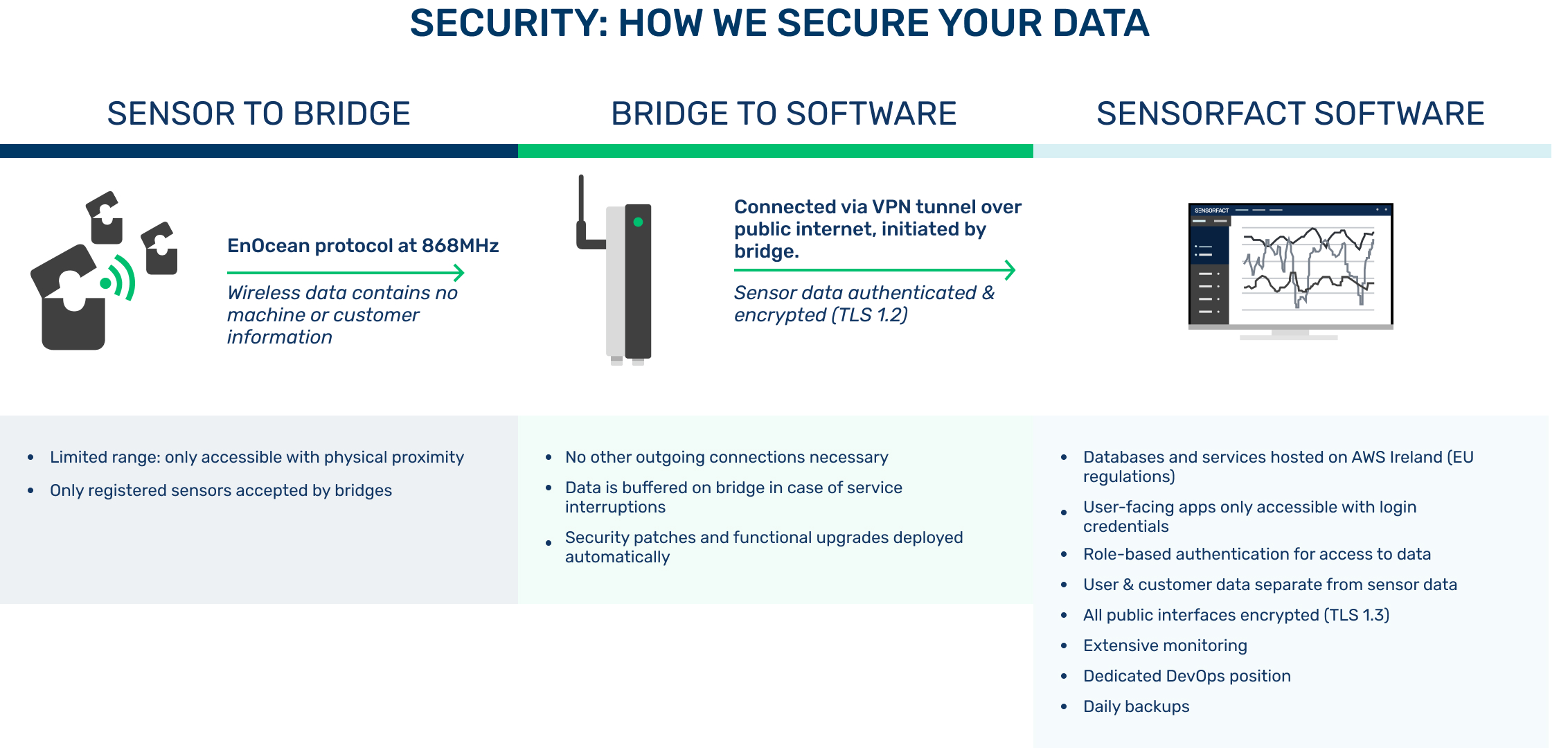
Sensorfact software application is cloud-based. Our entire IT infrastructure is hosted in AWS, using the region eu-west-1 (Ireland) for deployments, which is subject to EU regulations. Our software solutions are developed within our engineering team, and we do not employ third-party solutions apart from native services offered by AWS and distributed storage systems for our time measurements and streaming platform.
Authentication & Authorization
We can distinguish between customer access:
- Customers can access the Sensorfact Web portal with username and password credentials.
- The Onboarding team in Sensorfact creates accounts with minimal personal information (name, email address, and potentially phone number for alerts)
- There is no automatic renewal time for passwords.
- MFA authentication will be supported from Q3 2024
Additionally, employees at Sensorfact have access to the customer data following the next principles:
- Access to customer data by departments different from Engineering is restricted to personnel interacting with the customer.
- Engineers participating in the support rotations have access to all customer data, including production data, to debug and troubleshoot potential issues.
- We use PoLP as a main principle, and all the access to infrastructure and coding tools enforced MFA and access behind a VPN.
- Role-based authentication is used.
Data Management
Some of the key aspects to consider regarding data management:
- All public interfaces are encrypted (TLS 1.3)
- Data is not encrypted at rest.
- Customer data is logically segregated from other customer data
- Sensor and user/customer data (metadata) are physically stored separately.
- Backups: daily backups with an unlimited retention time.
- Customer personal data will be removed upon contract termination following GDPR guidelines.
Sensorfact have in place a Disaster Recovery Plan, which covers all the critical services and is tested regularly (at least two times per year frequency)
Incident Response Plan
The response plan to data breaches and security incidents is part of the global response plan for production issues and includes communication to customers affected with a clear description of the impact and how it has been solved.
Platform and IoT engineering support rotations are set in place to allow us to respond quickly to any production issues that could happen during working hours.
Proactive measure
With a yearly frequency, we perform penetration tests and infrastructure security audits, followed by an action plan to solve the findings depending on the severity. Critical findings are addressed immediately, and lower-impact ones are included in the Product Roadmap to be addressed throughout the year.